Your mobile user acquisition numbers look strong. Installs are climbing, CPA goals are being met, and your offer wall partners report high completion rates. But here is the uncomfortable reality: a significant portion of those installs and conversions may be coming from bots, device farms, and users gaming the system with residential proxies.
According to the 2025 Imperva Bad Bot Report, automated bot traffic now accounts for 51% of all internet activity, surpassing human traffic for the first time. The problem is especially severe on offer walls and rewarded ad placements, where the incentive structure creates a perfect environment for fraud.
What Is Mobile Ad Fraud?
Mobile ad fraud is any deliberate activity that manipulates mobile advertising metrics to generate illegitimate revenue. This includes faking app installs, simulating in-app events, hijacking attribution, and using bots to complete offer wall tasks.
The fraud exploits how mobile advertising works. Advertisers pay for specific actions: an install, a registration, reaching level 10 in a game, or making a first purchase. Fraudsters use automation, device manipulation, and proxy networks to trigger these events without real user engagement.
Unlike click fraud on desktop, mobile ad fraud often targets deeper funnel events. Advertisers moved to CPA models thinking it would protect them from fake clicks. Fraudsters adapted. They now simulate entire user journeys, from install to in-app purchase, using sophisticated bots that mimic human behavior.
The financial impact is staggering. Juniper Research estimates that advertisers lost $84 billion to ad fraud in 2023, with mobile accounting for a growing share as app marketing budgets expand.
Not sure if mobile ad fraud is affecting your campaigns?
Send us an export of your click and conversion data, and our team will provide a free audit of your mobile traffic. No strings attached.
App Install Fraud: The Foundation of Mobile Ad Fraud
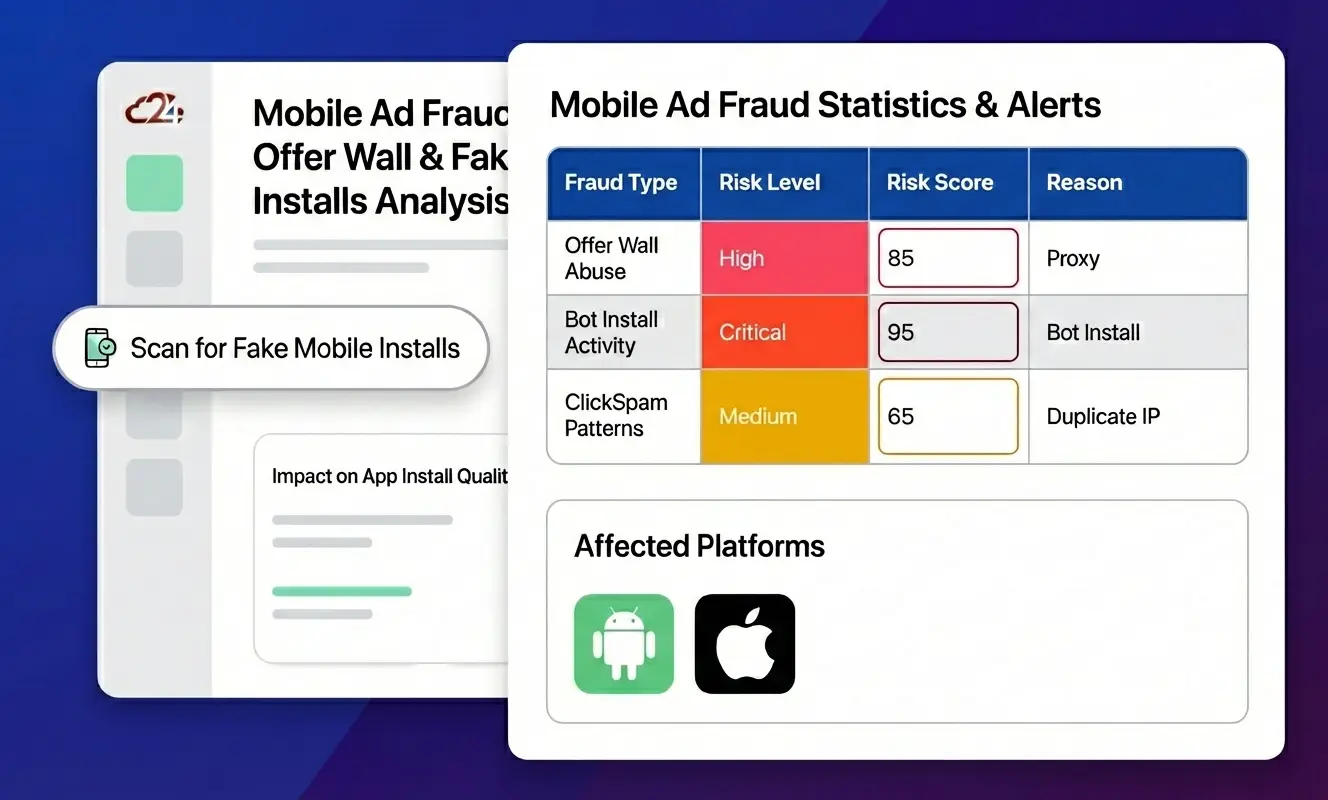
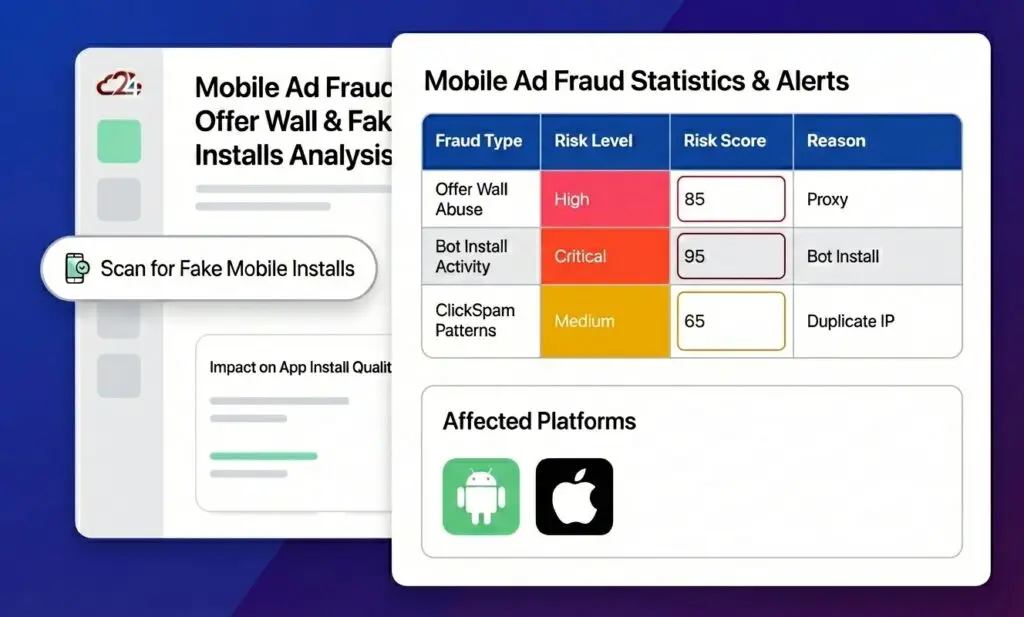
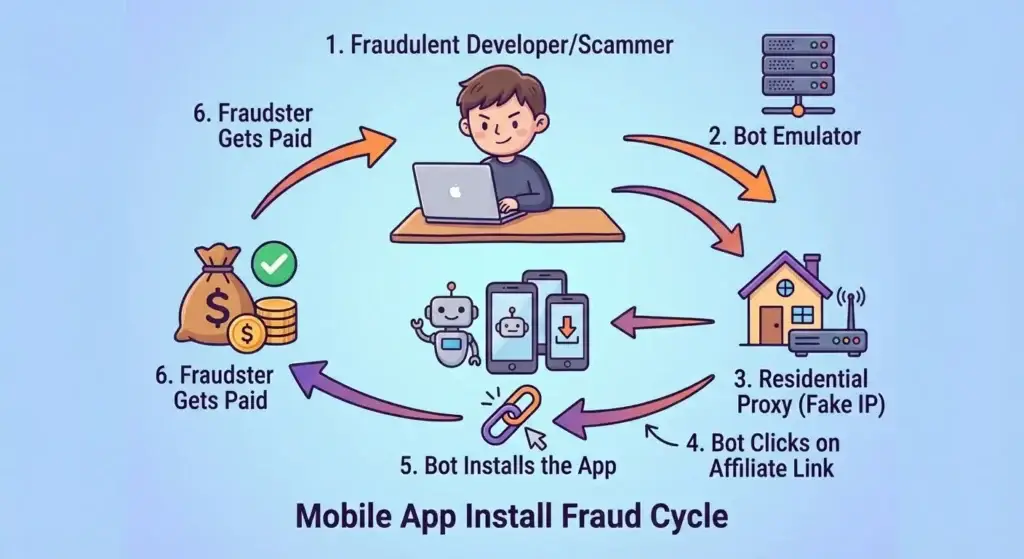
App install fraud occurs when fraudsters generate fake installs to collect CPI (cost per install) payouts. This is the most common form of mobile ad fraud and serves as the entry point for deeper funnel manipulation.
The methods vary in sophistication:
- Device farms: Physical locations with hundreds or thousands of real devices, operated by workers who manually install apps, complete tutorials, and reset device identifiers to repeat the process.
- Emulators and virtual machines: Software that simulates mobile devices, allowing fraudsters to generate thousands of fake installs from a single computer.
- SDK spoofing: Malware hidden in legitimate apps that sends fake install signals to attribution platforms without any actual install occurring.
- Click injection: Malicious apps that detect when a user is installing a new app and fire a fake click at the last moment to steal attribution credit.
- Click flooding: Generating massive volumes of fake clicks hoping that some will coincidentally match organic installs.
The challenge for advertisers is that these fake installs often look legitimate in attribution dashboards. The device IDs are real (or convincingly spoofed), the timing appears natural, and basic fraud filters miss them entirely.
Offer Wall Fraud: When Rewarded Offers Become a Target
Offer walls present a unique fraud challenge. These monetization tools reward users with virtual currency for completing advertiser tasks: downloading an app, signing up for a service, reaching a game milestone, or making a purchase.
The incentive structure that makes offer walls effective for user acquisition also makes them attractive to fraudsters. When completing an action earns coins, gems, or real money, bad actors will find ways to automate that process. The scale of this problem caught regulatory attention when the FTC settled with Tapjoy over hundreds of thousands of consumer complaints about fraudulent offer wall activity. The case highlighted how easily offer walls can be exploited when proper monitoring isn’t in place.
Common offer wall fraud tactics include:
- Bot automation: Using Selenium, Puppeteer, or AI-powered browser tools to automatically fill forms, complete signups, and simulate app usage.
- Residential proxy abuse: Routing traffic through real household IP addresses to bypass datacenter detection, making bot activity appear legitimate.
- Device ID cycling: Resetting advertising identifiers to complete the same offer multiple times from what appears to be different users.
- VPN manipulation: Spoofing geographic location to access higher-paying offers restricted to specific regions.
- Multi-accounting: Creating dozens of accounts to repeatedly claim rewards, often using disposable emails and fake identity data.
The 2025 Imperva Bad Bot Report reveals that 44% of advanced bot traffic now targets APIs and business logic, with form-based lead generation and offer walls among the primary attack vectors. As AI browser automation tools become more accessible, fraudsters can generate realistic form submissions that pass basic validation checks. The report found that 21% of all bot attacks now use residential proxies, making detection significantly harder.
Which Apps and Campaigns Are Most at Risk?
Mobile ad fraud disproportionately targets certain verticals and campaign types:
High-risk categories:
- Mobile gaming: High CPA payouts for reaching specific levels make games prime targets for device farms and bots.
- Finance and fintech: Lead generation campaigns paying $20 to $100+ per signup attract sophisticated fraud operations.
- Subscription services: Free trial offers get exploited by users creating multiple accounts with stolen or fake payment methods.
- Dating apps: Registration-based payouts lead to mass fake profile creation.
- Offer wall publishers: Any app monetizing through rewarded ads inherits the fraud risk from every advertiser on the wall.
High-risk campaign types:
- CPI campaigns without post-install event validation
- CPA campaigns with short attribution windows
- Offer wall placements in apps with young or gaming-focused audiences
- Incentivized traffic sources without proper disclosure
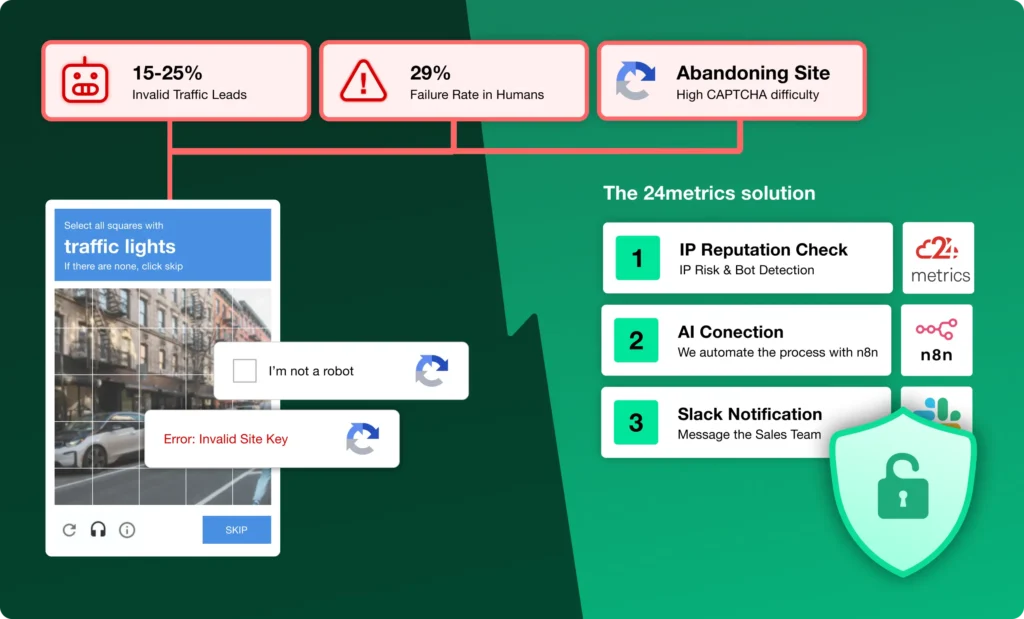
Research suggests that mobile ad fraud affects between 15% and 40% of traffic depending on the vertical and traffic sources used. For apps spending significant budgets on user acquisition, even the lower end of that range represents substantial waste.
How to Detect Mobile Ad Fraud
Mobile ad fraud leaves patterns in your data. Here are the red flags your team should monitor:
Attribution anomalies:
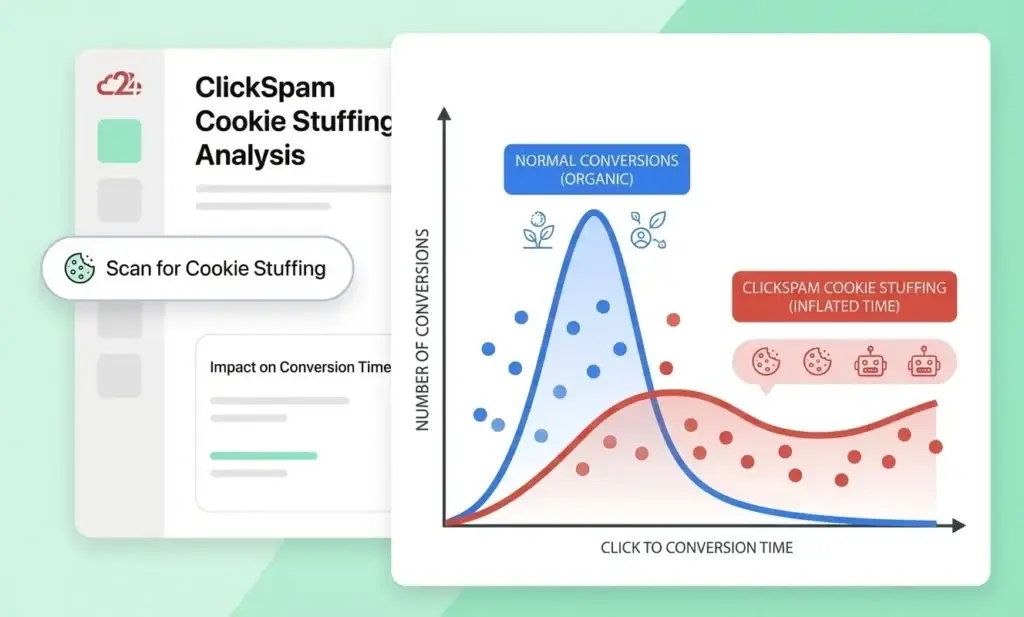
- Click-to-install times (CTIT) that are unusually short (under 10 seconds) or suspiciously long (days or weeks)
- High install volumes with near-zero post-install engagement
- Geographic mismatches between click location and install location
- Spikes in installs during off-hours or from unexpected regions
Behavioural signals:
- Users completing in-app events at inhuman speeds
- Identical session patterns across multiple users
- App opens without any subsequent activity
- Retention curves that drop to zero after day one
Technical indicators:
- High concentrations of traffic from VPNs, proxies, or datacenter IPs
- Device fingerprints that appear across multiple attribution sources
- Emulator or rooted device signatures in your install data
- SDK version mismatches suggesting spoofed installs
Offer wall specific patterns:
- Single users completing the same offer type repeatedly
- Completion rates that exceed statistical norms for your offer difficulty
- Form submissions with disposable email domains or sequential data patterns
Manual detection requires constant monitoring across potentially dozens of traffic sources and thousands of daily events. By the time anomalies become obvious, fraudsters have often collected significant payouts.
How to Stop Mobile Ad Fraud
Protecting your mobile campaigns requires screening at multiple points in the funnel.
Click-level protection blocks fraudulent traffic before it reaches your app. This prevents attribution manipulation and stops device farms from registering installs against your campaigns. Our click fraud detection platform identifies bot patterns, proxy traffic, and click injection attempts in real time.
Conversion-level screening validates that completed actions came from real users. This is critical for CPA campaigns and offer wall traffic where the install already occurred but the payout depends on deeper events. The affiliate fraud detection system at 24metrics analyzes behavioral signals, device fingerprints, and timing patterns to flag suspicious conversions before payouts are processed.
Integration with MMPs ensures fraud signals flow back to your attribution platform. We support direct integrations with Appsflyer, Adjust, Singular, and Branch, allowing you to automatically reject fraudulent installs and block postbacks to offending publishers.
The key is automated, real-time screening. Fraudsters operate at scale and adapt quickly. Manual review processes cannot keep pace. Our Anti Fraud Platform provides transparent rejection reasons for every blocked event, giving you the evidence needed to address fraud with your partners.
Protect Your Mobile Campaigns
Mobile ad fraud is not a hypothetical risk. It is an active drain on your budget happening right now. The shift to AI-powered bots, the proliferation of residential proxies, and the continued growth of offer wall monetization have created an environment where fraud is easier to execute and harder to detect than ever before.
If you are running mobile user acquisition campaigns with meaningful spend, you are a target. The question is whether your current tools are catching it.
Get a Free Traffic Audit
Not sure if mobile ad fraud is impacting your campaigns? Export your install and conversion data and send it to our team. We will analyze your traffic patterns, identify suspicious activity, and show you exactly where your budget may be leaking.