How to Detect Residential Proxies
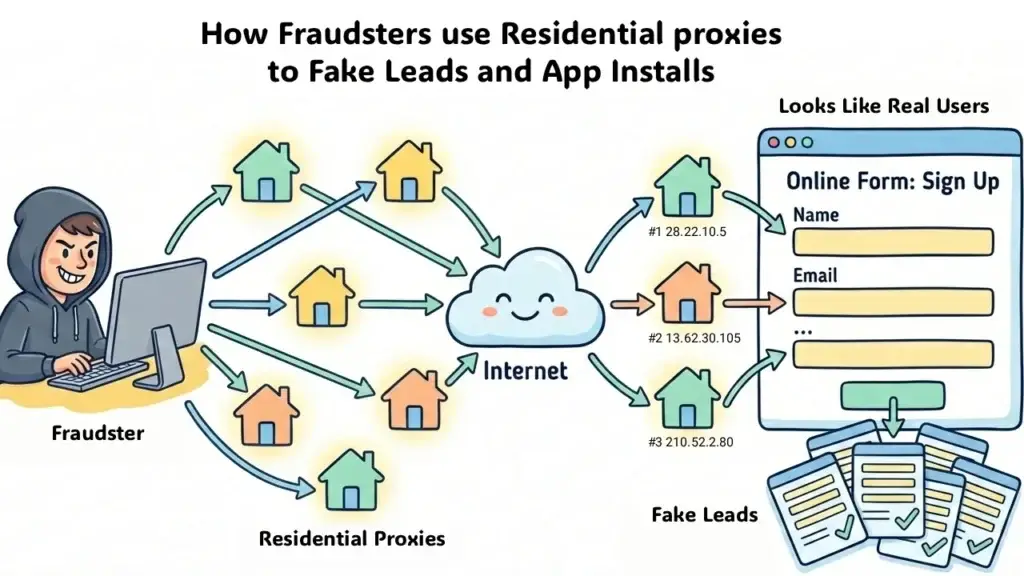
A residential proxy routes traffic through IP addresses assigned by Internet Service Providers to real home users. Unlike datacenter proxies that come from cloud servers with recognizable IP ranges, residential IPs look identical to legitimate consumer traffic.
This matters because most fraud detection relies on IP reputation databases. When a fraudster uses a datacenter IP, that address is already flagged. Residential proxies solve this problem by borrowing the reputation of real users.
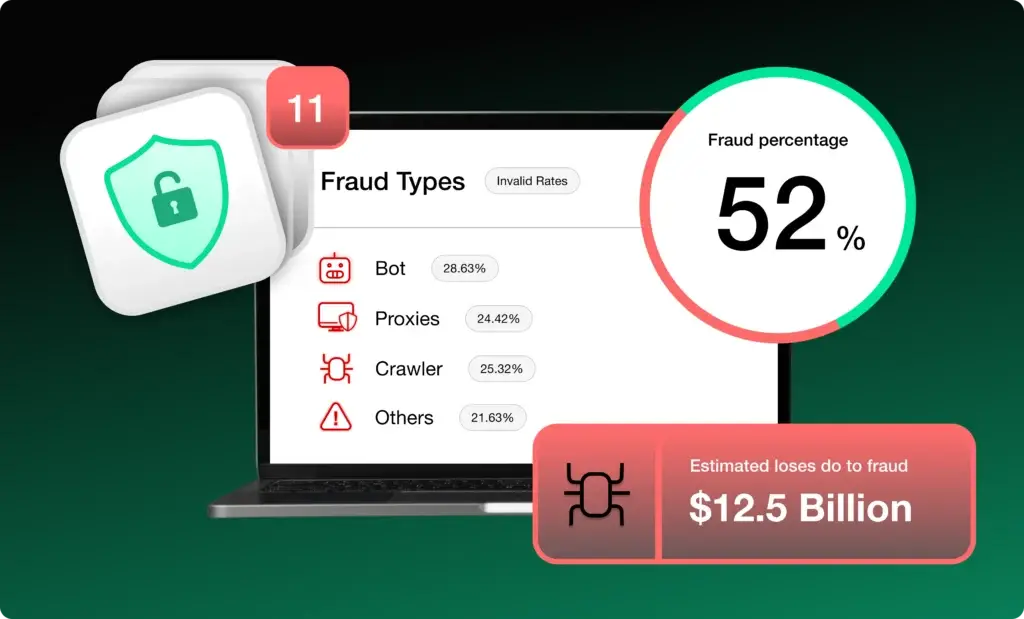
The shift has been dramatic. According to the 2024 Imperva Bad Bot Report, 25% of bad bot traffic now originates from residential ISPs. That number has grown every year for six consecutive years. Fraudsters running fake signups, click fraud operations, and attribution theft have learned that residential proxies are their path around traditional defenses.
The economics work in their favor. A residential proxy subscription costs between $5 and $15 per gigabyte. If a fraudster earns $50 per fake conversion and needs only a few megabytes of data per signup, the return on investment is substantial. They can rotate through millions of residential IPs, ensuring each fraudulent action appears to come from a unique, clean address.
Not sure if your Affiliates are sending you Bots & Residential IPs ?
Check if an IP belongs to a Bot, Click Farm, DataCenter, VPN or Residential Proxy.
What Are Residential Proxies and Why Do Fraudsters Use Them
A residential proxy routes traffic through IP addresses assigned by Internet Service Providers to real home users. Unlike datacenter proxies that come from cloud servers with recognizable IP ranges, residential IPs look identical to legitimate consumer traffic.
This matters because most fraud detection relies on IP reputation databases. When a fraudster uses a datacenter IP, that address is already flagged. Residential proxies solve this problem by borrowing the reputation of real users.
The shift has been dramatic. According to the 2024 Imperva Bad Bot Report, 25% of bad bot traffic now originates from residential ISPs. That number has grown every year for six consecutive years. Fraudsters running fake signups, click fraud operations, and attribution theft have learned that residential proxies are their path around traditional defenses.
The economics work in their favor. A residential proxy subscription costs between $5 and $15 per gigabyte. If a fraudster earns $50 per fake conversion and needs only a few megabytes of data per signup, the return on investment is substantial. They can rotate through millions of residential IPs, ensuring each fraudulent action appears to come from a unique, clean address.
The Difference Between VPNs, Datacenter Proxies, and Residential Proxies
Understanding the technical differences helps explain why residential proxies require specialized detection.
Datacenter Proxies originate from cloud hosting providers. Their IP ranges are well documented and often already present in blocklists. Detection is straightforward because the ASN (Autonomous System Number) immediately identifies the traffic source as a hosting company rather than an ISP.
VPNs encrypt user traffic and route it through servers operated by VPN providers. While some VPN providers use datacenter infrastructure, others have expanded into residential IP pools. Traditional VPN detection works by maintaining lists of known VPN server IPs, but this approach struggles when VPN providers rotate addresses frequently.
Residential Proxies use IP addresses assigned to actual homes. The traffic passes through devices owned by real people, often through SDK integrations in mobile apps or browser extensions where users have opted in (sometimes unknowingly) to share their connection. From a technical perspective, these IPs are indistinguishable from legitimate consumer traffic based on ASN or IP range alone.
This is why simple IP blocklists fail against residential proxy fraud. The IP address itself carries legitimate reputation because it belongs to a real person’s internet connection.
Industries Facing the Highest Residential Proxy Fraud
Residential proxy abuse concentrates in industries where fraudsters can monetize fake actions quickly.
Lead Generation attracts fraud because affiliates earn commissions per signup. Fraudsters submit fake leads using residential proxies to avoid duplicate detection and geo-restrictions. Each lead appears to come from a unique user in the target geography.
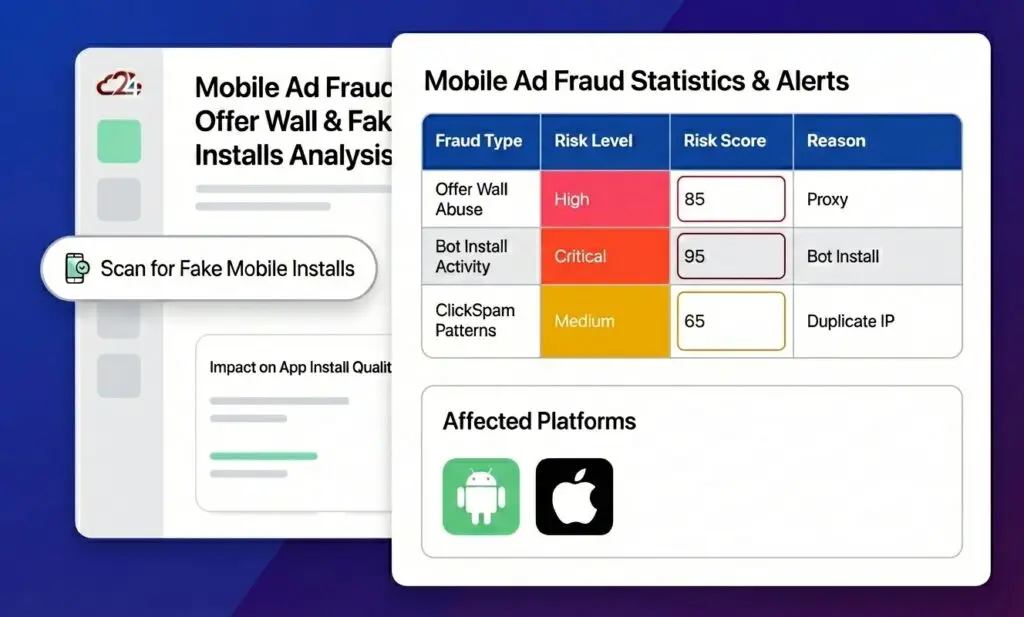
Mobile App Marketing faces click injection and fake install fraud. Residential proxies help fraudsters spoof device locations and bypass SDK-level protections. The 2024 Imperva report found that 44.8% of bad bots now masquerade as mobile user agents, often combined with residential proxy usage.
Dating Platforms deal with fake profile creation at scale. Fraudsters create accounts to earn affiliate commissions or run romance scams. Residential proxies let them appear as local users while operating from anywhere in the world.
Gaming and Betting platforms see bonus abuse and multi-accounting. Players create duplicate accounts to exploit welcome offers. Residential proxies from the target country help them bypass location restrictions and device fingerprinting.
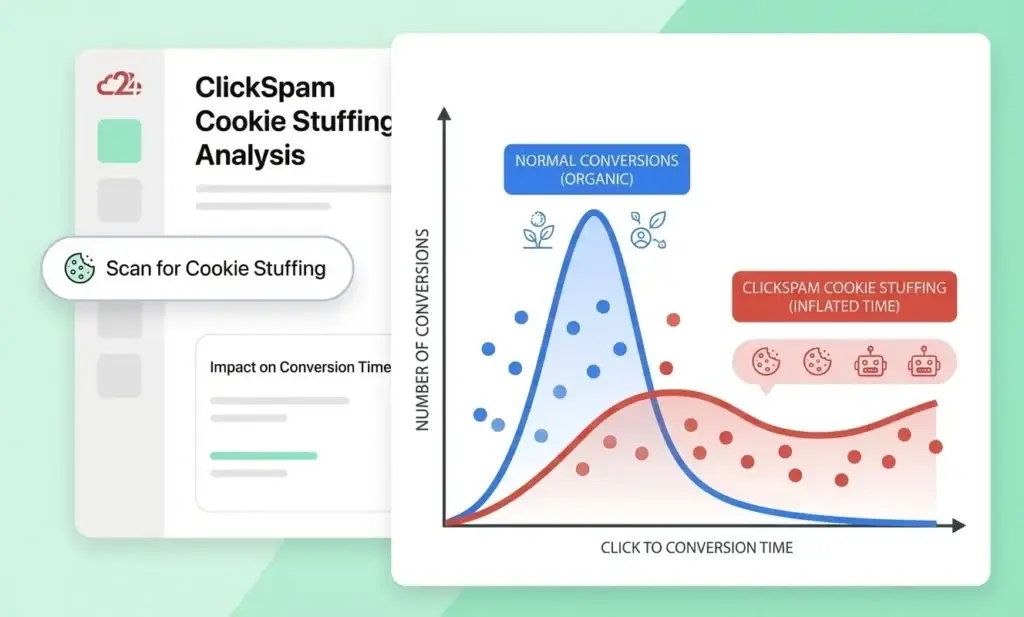
eCommerce Affiliate Programs experience cookie stuffing and attribution theft. Fraudsters claim credit for organic sales by dropping cookies through residential proxy traffic that appears legitimate. Probabilistic attribution models can be abused through residential proxies.
How Honeypot Networks Detect Residential Proxies
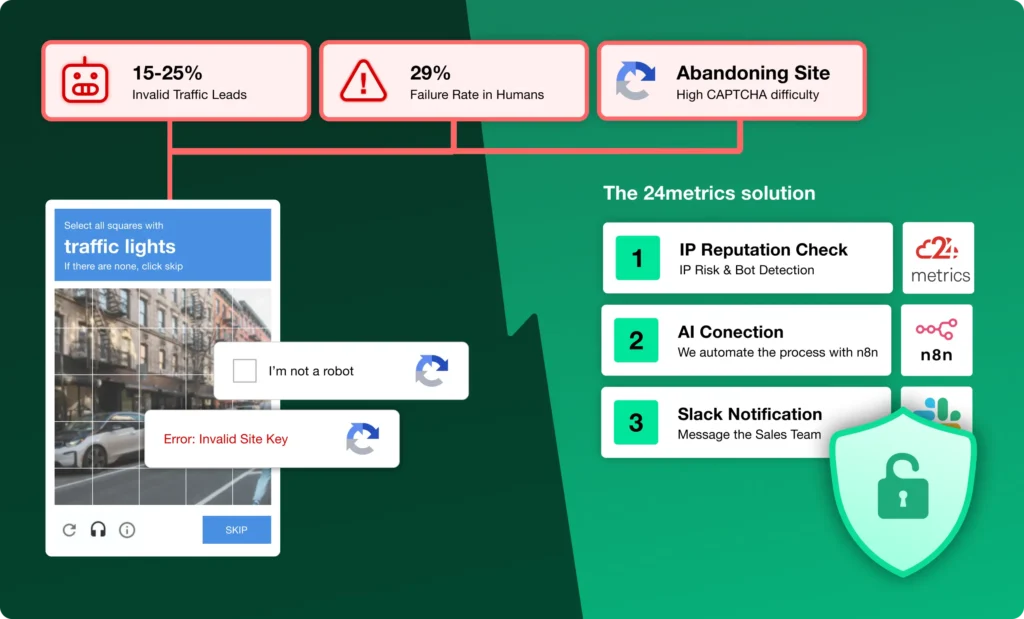
Traditional IP blocklists update once per day at best. A residential proxy provider can rotate through thousands of IPs in that time, staying ahead of static lists.
Honeypot networks take a different approach. Instead of relying on third-party lists, a honeypot deploys tracking across thousands of websites to identify IPs exhibiting proxy behavior in real time.
At 24metrics, our honeypot network monitors approximately 12 million IPs globally, including roughly 1 million residential IPs in the United States alone. When our system detects an IP being used as a proxy, that address is blacklisted immediately. There is no 24-hour delay waiting for a database update.
The honeypot works by creating scenarios that reveal proxy usage. These might include timing analysis that detects multiple geographically distant requests from the same IP within impossible timeframes, or behavioral patterns that indicate traffic routing rather than direct connections. When an IP triggers these indicators, the system flags it before that address can be used to commit fraud on protected campaigns.
This real-time capability matters because residential proxy providers constantly refresh their IP pools. An IP might be clean in the morning and compromised by afternoon. Detection systems that rely on daily updates will miss these newly recruited addresses.
Beyond IP Lists: Behavioral Detection Methods
Effective residential proxy detection cannot depend solely on IP reputation. The most sophisticated approach combines multiple signals.
Location Mismatch Analysis compares the reported IP geolocation against other indicators. If an IP claims to be in Chicago but the browser timezone is set to Moscow, or the device language is configured for Russian, that inconsistency suggests proxy usage. Fraudsters often forget to align all location signals when routing through residential proxies.
Latency Measurement examines connection timing. Traffic routed through a residential proxy in another country introduces measurable delay. If a user claims to be in New York but their connection latency suggests the traffic is traveling across an ocean, that IP deserves scrutiny.
Connection Fingerprinting looks at TCP/IP stack characteristics, WebRTC leaks, and other technical markers that can reveal when traffic is being routed rather than connecting directly. These fingerprints are difficult for proxy operators to mask completely.
Behavioral Patterns track how traffic from specific IPs behaves over time. A residential IP that generates hundreds of signups across multiple affiliate programs is clearly being used as a proxy, even if it has never appeared on a blocklist.
Our detection combines all these methods. We do not depend on any single signal, which reduces false positives while catching fraud that would slip past simpler systems.
What Proxy Rates Are Normal vs. Fraudulent
Not all proxy traffic is fraud. Privacy-conscious users run VPNs. Business travelers connect through corporate proxies. Hotel and airport WiFi networks often route through centralized gateways that appear as proxy traffic.
Based on analysis across hundreds of millions of clicks, legitimate traffic sources typically show less than 5% VPN and proxy usage. This benchmark helps distinguish normal variation from fraud patterns.
The difference between 3% and 50% proxy traffic is not just quantitative. A source running 3% might have a few privacy-focused users. A source running 50% is almost certainly sending manufactured traffic.
Smart detection systems apply thresholds contextually. Traffic from a hotel booking site will naturally show higher proxy rates than traffic from a local services app. Our algorithms account for these edge cases automatically, avoiding false flags on legitimate traffic patterns while catching sources that deviate significantly from expected baselines.
This threshold-based approach matters for advertiser relationships. Blocking all proxy traffic generates complaints from legitimate users and damages conversion rates. Blocking only sources with abnormal proxy concentrations targets actual fraud without collateral damage.
Best Practices for Stopping Residential Proxy Fraud
Protecting campaigns from residential proxy fraud requires a layered approach.
Deploy Real-Time Detection rather than relying on daily blocklist updates. Residential proxy providers refresh their IP pools constantly. Detection that operates in real time catches newly recruited proxies before they can be used against your campaigns.
Combine Multiple Signals instead of depending on IP reputation alone. Behavioral analysis, location verification, and latency measurement together create a detection system that fraudsters cannot easily bypass by switching proxy providers.
Set Appropriate Thresholds for your industry and traffic sources. Blocking all proxy traffic creates false positives. Monitoring proxy percentages by source and flagging anomalies catches fraud patterns without disrupting legitimate traffic.
Analyze at the Source Level rather than just individual clicks or conversions. A single proxy click might be a privacy-conscious user. A source sending 40% proxy traffic is running a fraud operation.
Use Transparent Rejection Reasons so publishers understand why traffic was flagged. Standardized codes like “residential proxy detected” or “location mismatch” create accountability and help legitimate partners clean up their traffic sources.
Conclusion
Residential proxies have fundamentally changed affiliate fraud. Traditional datacenter detection and static IP blocklists cannot keep pace with providers that rotate through millions of legitimate-looking addresses.
Effective detection requires real-time honeypot networks that identify proxy IPs as they emerge, behavioral analysis that catches location and timing inconsistencies, and threshold monitoring that distinguishes normal privacy tool usage from fraud patterns.
The 5% threshold provides a useful baseline. Sources below that level warrant monitoring. Sources significantly above it require investigation or blocking.
Get a Free Traffic Audit
Not sure if residential proxies are impacting your campaigns ? Export your conversion data and send it to our team. We will analyze it and let you if your traffic is fake or not.